Once the project risk management scope and objectives are agreed upon, it is possible to start the risk identification process. A variety of risk identification techniques is available, each with its own characteristics.
What is Risk Identification?
is the process of identifying individual project risks as well as sources of overall project risk, and documenting their characteristics. The key benefit of this process is the documentation of existing individual project risks and the sources of overall project risk. It also brings together information so the project team can respond appropriately to identified risks.
The aim is to expose and document all knowable risks, recognizing that some risks will be inherently unknowable and others will emerge later in the project. The emergent nature of risk requires the risk identification process to be iterative, in order to find risks that were not evident earlier in the project.
Input should be sought from a wide range of project stakeholders throughout the risk identification process since each will have a different perspective on the risks facing the project. Historical records and project documents should also be reviewed to identify risks for this project.
Risk identification considers both individual project risks and sources of overall project risk. Participants in risk identification activities may include the following: project manager, project team members, project
risk specialist (if assigned), customers, subject matter experts from outside the project team, end users, other project managers, operations managers, stakeholders, and risk management experts within the organization.
While this personnel is often a key participant in risk identification, all project stakeholders should be encouraged to identify individual project risks. It is particularly important to involve the project team so they can develop and maintain a sense of ownership and responsibility for identified individual project risks, the level of overall project risk, and associated risk response actions.
When describing and recording individual project risks, a consistent format should be used for risk statements to ensure that each risk is understood clearly and unambiguously in order to support effective analysis and risk response development.
Risk owners for individual project risks may be nominated as part of the risk identification process and will be confirmed during the qualitative risk analysis process.
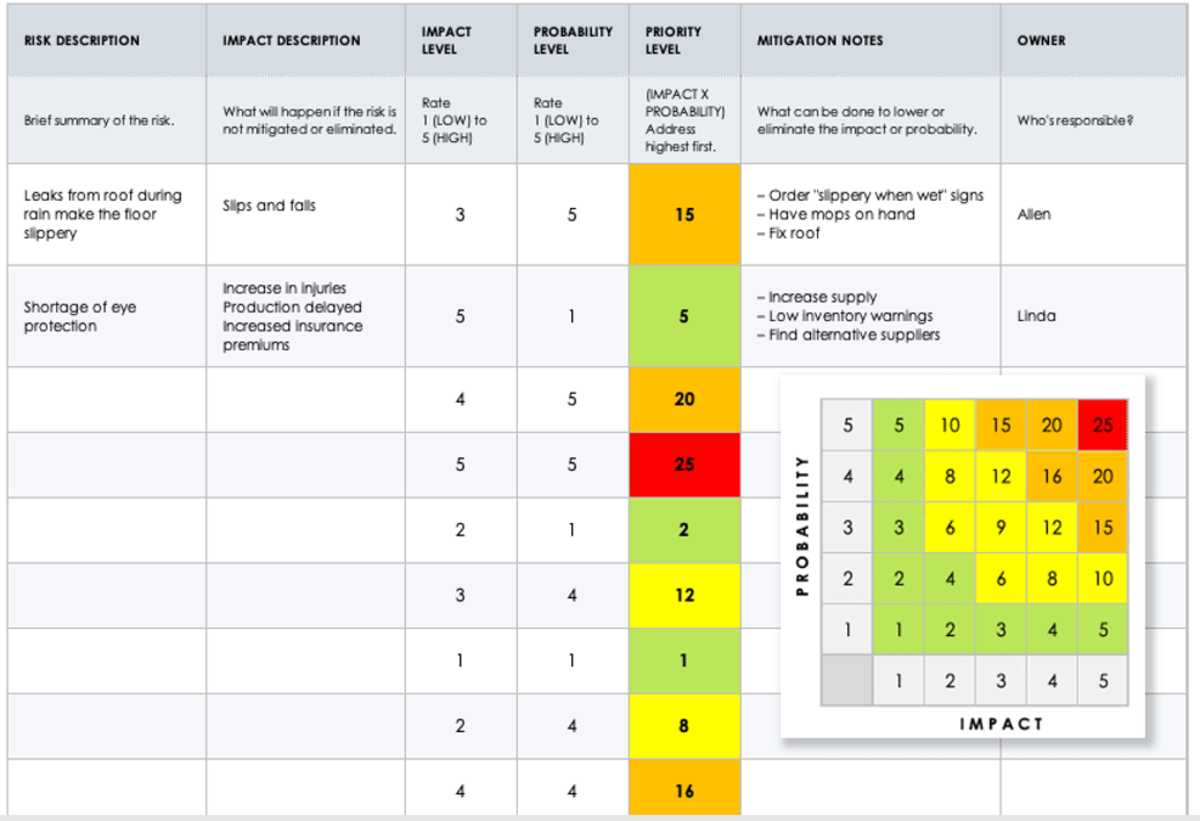
Risk Identification example
To avoid any confusion, you need to use the cause–risk–effect format. As a result of (Definitive cause), (Uncertain event) may occur, which would lead to (effect).
Example: As a result of the lack of clear scope of the hotel lobby part, there could be rework and waste of effort which would delay the project's critical path by 2 weeks. To confirm that this is an effect, it shall relate to project objectives, project constraints, and risk tolerances.
Common Risk Identification Tools and Techniques
A range of risk identification methods, tools, and techniques is available for risk identification in project management, below are some of the commonly used ones:
Brainstorming: The goal of brainstorming is to obtain a comprehensive list of individual project risks and sources of overall project risk. The project team usually performs brainstorming, often with a multidisciplinary set of experts who are not part of the team.
Ideas are generated under the guidance of a facilitator, either in a free-form brainstorming session or one that uses more structured techniques. Categories of risk, such as in a risk breakdown structure, can be used as a framework. Particular attention should be paid to ensuring that risks identified through brainstorming are clearly described since the technique can result in ideas that are not fully formed.
Interviews: Individual project risks and sources of overall project risk can be identified by interviewing experienced project participants, stakeholders, and subject matter experts. Interviews should be conducted in an environment of trust and confidentiality to encourage honest and unbiased contributions.
Root cause analysis: Root cause analysis is typically used to discover the underlying causes that lead to a problem, and develop preventive action. It can be used in the risk identification process to identify threats by starting with a problem statement (for example, the project might be delayed or over budget) and exploring which threats might result in that problem occurring.
SWOT analysis: This technique examines the project from each of the strengths, weaknesses, opportunities, and threats (SWOT) perspectives. Risk identification is used to increase the breadth of identified risks by including internally generated risks. The technique starts with the identification of strengths and weaknesses of the organization, focusing on either the project, organization or the business area in general.
Prompt Lists: A prompt list is a predetermined list of risk categories that might give rise to individual project risks and that could also act as sources of overall project risk. The prompt list can be used as a framework to aid the project team in idea generation when using risk identification techniques. The risk categories in the lowest level of the risk breakdown structure can be used as a prompt list for individual project risks.
Some common strategic frameworks are more suitable for risk identification for example PESTLE (political, economic, social, technological, legal, environmental).
Conduct a “Pre-Mortem”: It’s a meeting to come up with ideas. The assembled group is asked to imagine that the project is completed or has been terminated, or it has failed to meet one or more of its objectives. The group is then asked to describe why the project has failed, the same shall be repeated while imagining the project is a success to find the opportunities.
Risk Register
After completion of the risk identification process, you will have the risk register as the key output.
The risk register captures details of identified individual project risks. The results of Perform Qualitative Risk Analysis, Plan Risk Responses, Implement Risk Responses, and Monitor Risks are recorded in the risk register as those processes are conducted throughout the project. The risk register may contain limited or extensive risk information depending on project variables such as size and complexity.
On completion of the risk identification process, the content of the risk register may include but is not limited to
List of identified risks: Each individual project risk is given a unique identifier in the risk register. Identified risks are described in as much detail as required to ensure unambiguous understanding. A structured risk statement may be used to distinguish risks from their cause(s) and their effect(s).
Potential risk owners: Where a potential risk owner has been identified during the Identify Risks process, the risk owner is recorded in the risk register.
List of potential risk responses: Where a potential risk response has been identified during the Identify Risks process, it is recorded in the risk register.
Additional data may be recorded for each identified risk, depending on the risk register format specified in the risk management plan. This may include a short risk title, risk category, current risk status, one or more causes, one or more effects on objectives, risk triggers, WBS reference of affected activities, and timing information.
Risk Report
After completion of the risk identification process, you will have the risk report as one of the key outputs.
The risk report presents information on sources of overall project risk, together with summary information on identified individual project risks. The risk report is developed progressively throughout the Project Risk Management process.
The results of Perform Qualitative Risk Analysis, Perform Quantitative Risk Analysis, Plan Risk Responses, Implement Risk Responses, and Monitor Risks are also included in the risk report as those processes are completed.
On completion of the risk identification process, information in the risk report may include but is not limited to: Sources of overall project risk, indicating which are the most important drivers of overall project risk exposure; and summary information on identified individual project risks, such as a number of identified threats and opportunities, distribution of risks across risk categories, metrics and trends, etc.
Conclusion
In conclusion, risk cannot be managed unless it is first identified. Consequently, after risk management planning has been completed, the first process in the iterative Project Risk Management process aims to identify all the knowable risks to project objectives.
The purpose of risk identification is to identify risks to the maximum extent that is practicable. The fact that some risks are unknowable or emergent requires the Identify Risk process to be iterative, repeating the risk identification process to find new risks which have become knowable since the previous iteration of the process.
When a risk is first identified, potential responses may also be identified at the same time. These should be recorded during the risk identification process and considered for immediate action if such action is appropriate. Where such responses are not implemented immediately, these should be considered during the Plan Risk Responses process.
If what we explained in this article is part of your day-to-day job, or if you are interested in improving your knowledge in the risk management field, we highly recommend you read about the PMI RMP certification exam through the link here. Also, you can have a look at the curriculum of our PMI RMP exam perpetration workshop through the link here.

.jpg)
.jpg)
.jpg)


